Unified endpoint management (UEM) and digital experience monitoring (DEM) solutions have complementary capabilities focused on endpoint management and user experience. While UEM solutions provide a comprehensive view into the endpoint environment, DEM solutions offer deep insights into the user experience across modern SaaS, web and cloud-hosted applications, and the dynamic, internet-based networks used to access them. Organizations often use endpoint monitoring and digital experience solutions in combination to gain a more complete view across their infrastructure, applications, and the resulting digital experience.
Let’s examine their differences and synergies.
What is Unified Endpoint Management?
Unified Endpoint Management (UEM), refers to the practice of managing and securing endpoint devices such as desktop computers, laptops, smartphones, tablets, and IoT devices. The goal of endpoint device management is to ensure that these devices are properly configured, maintained, and secured to protect against data breaches, malware infections, and other security threats.
Endpoint management involves a range of activities, including:
- device inventory tracking and policy management
- software installation and application management
- device configuration and patch management
- security policy enforcement
- endpoint device performance monitoring
In addition, some UEM products include tools that track end-user activity or detect and remediate security issues. Endpoint monitoring vendors include SolarWinds, Nagios, Datadog, Lakeside, 1E, Zabbix, Splunk, and ManageEngine, to name a few.
What is Digital Experience Monitoring?
Digital Experience Monitoring (DEM) is designed to monitor the user experience across digital channels, including cloud and SaaS applications, and provide insights into performance, availability and user experience in real-time.
- DEM is intended for use in modern digital environments, such as cloud and SaaS applications, as well as remote and distributed workforces supporting bring your own device (BYOD) policies.
- It tracks application performance, such as load times, page load speed, and how well the application functions from the user’s point of view.
- DEM provides a comprehensive view of the user experience, including how users interact with an application and potential performance bottlenecks.
How is UEM Deployed?
Endpoint monitoring can be deployed in a variety of ways depending on the organization’s needs and infrastructure. Here are some common deployment methods for endpoint monitoring:
- Agent-based deployment: A monitoring agent is installed on each endpoint. The agent sends endpoint data to a monitoring server, which analyzes the data, provides alerts, device management and remediation capabilities. An agent-based approach is required to monitor specific applications or system processes.
- Agentless deployment: SNMP or WMI protocols are used to collect endpoint data by the monitoring solution. This method is used for basic monitoring needs like endpoint availability.
- Cloud-based deployment: Endpoints transmit data to a cloud-based server, which aggregates the information and generates insights and alerts. Because it eliminates the need for on-premise monitoring servers, this method is typically used when monitoring a large number of endpoints.
- Hybrid deployment: This method uses a combination of agent-based and agentless monitoring approaches. An agentless solution may be used to monitor endpoint availability, while an agent-based solution monitors specific applications or processes.
Endpoint monitoring solutions can potentially introduce security risks if not implemented and managed properly. For example, if the monitoring software is not properly secured, it can potentially be exploited by attackers to gain unauthorized access to the monitored devices or network.
Additionally, some endpoint monitoring solutions can have an impact on device performance, as they require processing power and memory resources to run. This can be especially noticeable on older or resource-constrained devices.
Factors such as the number of endpoints, the level of monitoring required, and the infrastructure in place will all play a role in determining the best deployment method for endpoint monitoring.
How is DEM Deployed?
Digital Experience Monitoring (DEM) is typically deployed in the following ways:
- Agent-based monitoring: To collect data and report performance issues to the DEM system, an agent is installed on end-user devices or servers. Agents should be used only when necessary because they add work to the computer being monitored, slowing it down and making it less secure.
- Synthetic monitoring: To simulate user interactions and measure performance metrics, artificial traffic is generated from remote locations. This approach has limitations, such as a lack of fidelity with real-world user behavior and high maintenance requirements to keep scripted scenarios up to date with rapidly changing SaaS applications and CI/CD-centric deployment models.
- Real-user monitoring (RUM): Performance data is collected from real users interacting with the digital service via their browsers or mobile devices. Agents are no longer used in modern RUM solutions to monitor SaaS and web-based apps. Instead, they employ lightweight browser extensions.
- Network monitoring: To assess the impact on digital experience, metrics such as latency, bandwidth, and packet loss are collected and analyzed. Network visualization and tracing for BGP routes and Internet traffic assists network administrators in better understanding how traffic moves across the network, identifying bottlenecks, and improving overall network performance.
The focus of a DEM deployment will be determined by the organization’s specific needs and goals. In all cases, DEM employs a combination of network, application, and real user monitoring insights to allow IT teams to rapidly troubleshoot and proactively optimize digital experience from the users’ context and perspective.
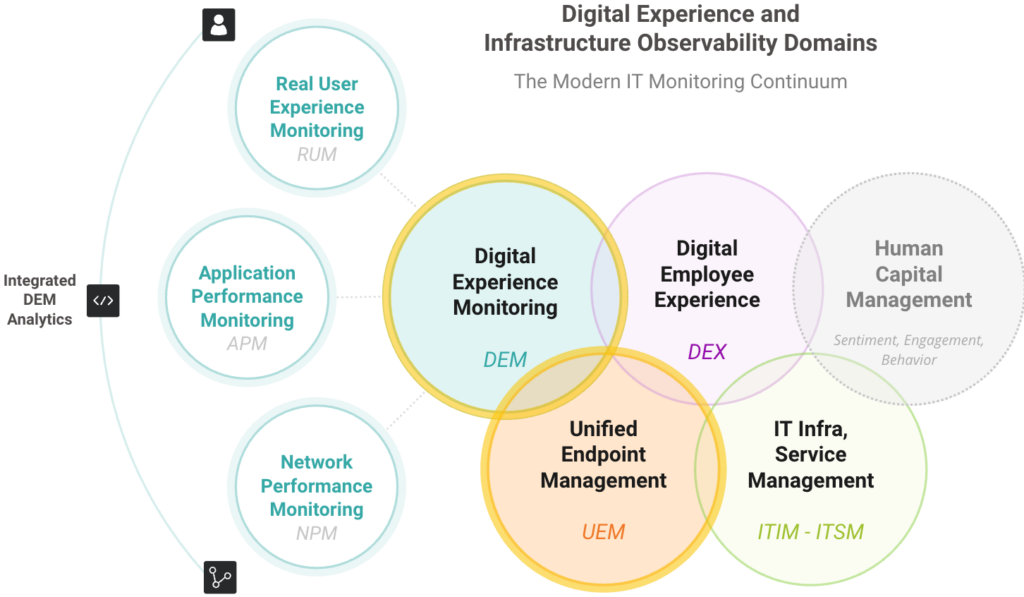
How Does DEM Compare to UEM?
The diagram above based on our DEM infographic illustrates the relationship between UEM and DEM within the modern digital experience and performance monitoring observability spectrum.
While unified endpoint management is a distinct domain, digital experience monitoring incorporates endpoint performance and utilization metrics to assess how device performance impacts digital experience and application responsiveness.
The massive adoption of web, cloud, and SaaS applications supported by dynamic SD WAN, internet, cloud and hybrid networks mean that the vast majority of application performance issues impacting digital experience no longer originate from device performance issues.
DEM solutions allow IT teams to quickly determine the root cause of the performance degradation and prioritize remediation efforts. By answering the most difficult question, “Is this issue caused by the device, the network, or (cloud-based) application hosting?” digital experience monitoring identifies which domain-specific tools should be used to provide more insight, if required: e.g. UEM, APM, NPM, or cloud-observability.
For a complete comparison, see the table below.
| DEM | UEM | |
| Use Cases | Monitoring, troubleshooting and and optimizing: | Monitoring and managing: |
| SaaS Performance | Hardware devices (desktop, mobile, IoT) | |
| Cloud, internet SD WAN performance | Software and components | |
| Employee digital experience | Security posture and policy compliance | |
| Customer digital experience | Remediation of device-centric issues | |
| WFH productivity | User activity | |
| Business efficiency | Device and software updates | |
| Cloud/SaaS migration | ||
| SD WAN migration | ||
| CASB / ZTNA performance | ||
| Used By | IT Operations | Digital workplace owners |
| Network Operations | Service desk technicians | |
| Application Owners | IT and system admins | |
| Service Desk | SecOps teams | |
| SRE / DevOps | Compliance officers | |
| Contact Center Managers | ||
| Pros | Complements UEM solutions with visibility into digital experience, SaaS, cloud, WFH and hybrid network performance | Simplified endpoint management from a single console - reduces the need to use multiple tools and systems to manage devices, software and security |
| SaaS-based, cost efficient and easy to deploy | Manages automated software deployment, updates and configuration | |
| Easy to deploy and scale | Integrated with security and identity management systems | |
| No dependency on hardware or agents | ||
| No impact on device performance or security | ||
| Not affected by encrypted traffic | ||
| Cons | New, maturing technology | Limited insight into user experience, network and application performance, and cloud-based infrastructure |
| Limited visibility into legacy / thick-client and native mobile applications | May be complex to deploy where agents are required | |
| Some DEM solutions built on legacy APM/RUM technology deliver only partial visibility | May impact endpoint device performance and security | |
| Benefits | Accelerates MTTR across complex, modern apps and infrastructure | Improved security and compliance |
| Permits evidence-based vendor management | Unified endpoint visibility across all users, locations, and device types | |
| Focuses IT efforts on outcomes instead of alarms | Increased IT efficiency: automation of routine maintenance tasks | |
| Provides end-to-end insight and analytics for proactive performance optimization | Reduced downtime with proactive device maintenance | |
| Optimizes employee productivity, experience and retention | Improved user experience and productivity with optimal device and software performance | |
| Reduces risk in digital migration projects | Cost savings: streamlining IT and reducing manual effort. |
What are the Limitations of Endpoint Management Software?
Endpoint management software also has some limitations that should be considered, including:
- Incomplete Coverage: Endpoint management software may not cover all types of endpoints, such as legacy or IoT devices.
- Compatibility Issues: Endpoint management software may not be compatible with all types of hardware and software, which can limit its usefulness and create additional management challenges.
- Complexity: Endpoint management software can be complex to set up and configure, requiring a high level of expertise and resources.
- False Positives: Endpoint management software may generate false positives, which can lead to unnecessary alerts and time-consuming investigations. This can also reduce the credibility of the alerts and cause IT teams to ignore them.
- Resource Intensive: Endpoint management software can require a significant amount of bandwidth and storage to manage, fund and maintain.
- Limited Scope: UEM does not provide insight into how end-users interact with applications or their digital experience, nor does it provide a clear view of where and how network performance affects it.
What are the Benefits of DEM?
Digital experience monitoring is essential to monitor, maintain and optimize the performance of SaaS, web and cloud applications for five main reasons:
- User Satisfaction: In today’s competitive digital landscape, user experience is a critical factor in determining an application’s success. DEM enables the measurement and monitoring of user satisfaction, which is critical for customer retention and growth.
- Performance Optimization: DEM provides real-time visibility into an application’s performance and potential bottlenecks. This data can be used by IT, DevOps, and service delivery teams to optimize application performance, even if the problem originates within the infrastructure of the SaaS vendor or a service provider’s network.
- Troubleshooting: DEM can assist in more quickly locating and resolving problems, resulting in less downtime and increased application availability. Bottlenecks may be promptly located and diagnosed thanks to visibility across user context, device and browser performance, internet, hybrid, and zero trust network access, and the performance of all hostnames serving SaaS and integrated apps.
- Compliance: Many organizations are required to follow laws that demand data sovereignty and application performance monitoring and reporting. DEM can assist businesses in fulfilling these requirements and proving their commitment to upholding the highest levels of security, performance, and availability.
- Employee Productivity: Effective digital experience monitoring enables IT organizations to optimize the performance of mission-critical applications for all employees, resulting in increased productivity and business performance.
Is DEM Cost Effective?
Digital Experience Monitoring (DEM) can be cost-effective, particularly in large-scale networks, multi-cloud environments, and SaaS-centric enterprises with dispersed users, sites, and branch offices.
Because they enable organizations to proactively monitor and optimize the performance and quality of their digital services and applications without complex deployment and hardware requirements, SaaS-based and agent-free DEM solutions are the most cost-effective and provide tangible business benefits.
This leads to increased customer satisfaction, decreased downtime, and lower costs associated with resolving performance issues, allowing IT to ultimately save money and improve the bottom line, resulting in a quick ROI.
DEM and UEM, Better Together?
While UEM can provide visibility into device-level performance, it does not provide the same level of insight into how end-users are interacting with applications. As a result, digital experience monitoring (DEM) is often seen as essential for UEM users because it provides insight into the end-user experience.
DEM solutions can help UEM users to better understand how applications are functioning on managed devices, as well as how employees are engaging with those applications. For example, if a UEM solution detects a slow response time when accessing a SaaS application, it can use the information from the DEM solution to identify the root cause of the problem and resolve it in a timely manner. This can include optimizing network connectivity, checking for compatibility issues, or addressing resource constraints on the device.
By combining the strengths of UEM and DEM, organizations can ensure that their end-users have a seamless and reliable experience when accessing SaaS applications, even when working from remote locations. This can improve productivity and help to ensure that the organization’s IT infrastructure is able to support the demands of the modern, hybrid workplace.
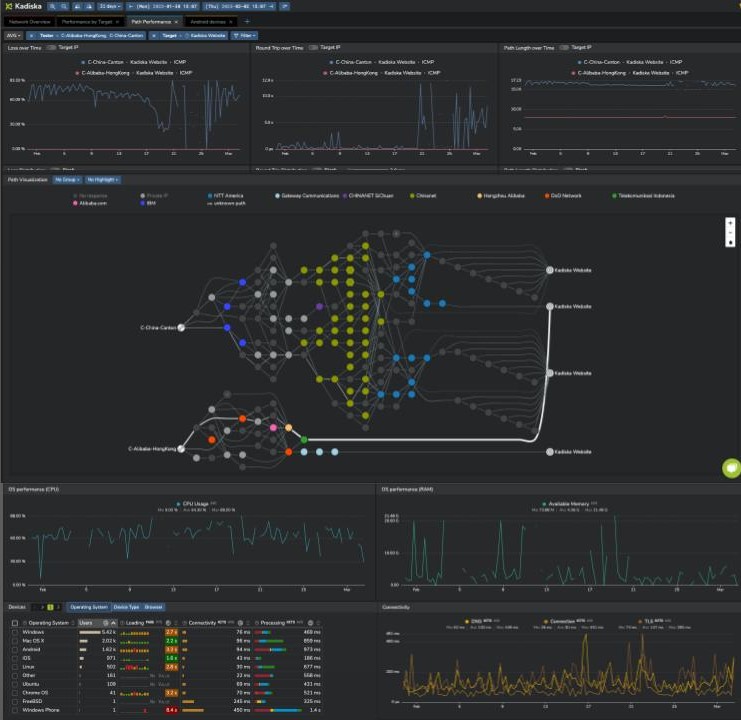
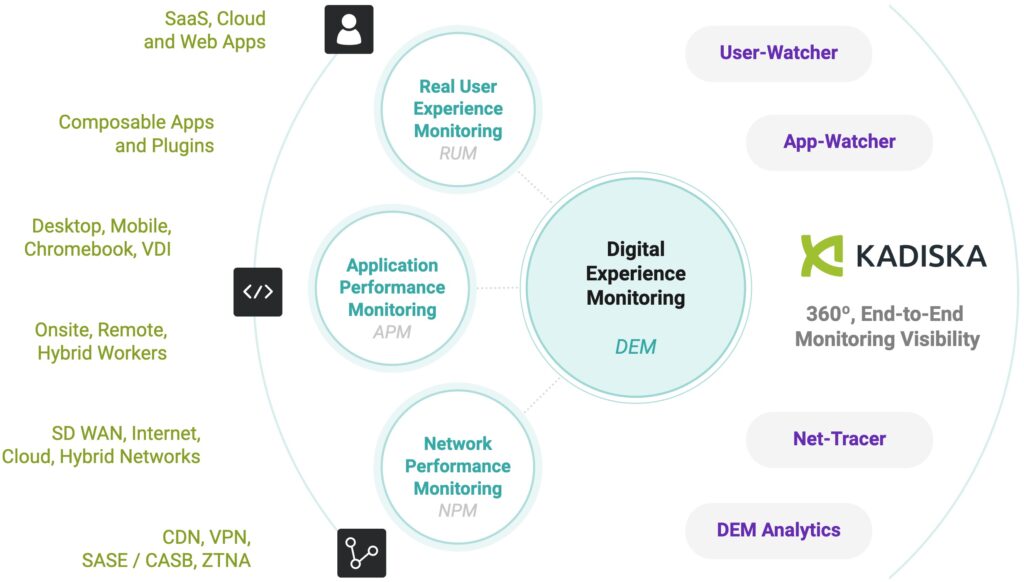
The Kadiska Digital Experience Platform
Kadiska is a complete, modern digital experience monitoring platform that provides a 360-degree view of real user experiences, network performance, and application monitoring across hybrid cloud, SaaS, and PaaS hosting platforms, where traditional endpoint management and monitoring solutions lack visibility.
This enables IT teams to proactively identify, isolate, and fix digital experience performance issues. The platform provides real user monitoring, application experience monitoring, and network path and performance monitoring using information gathered from multiple sources.