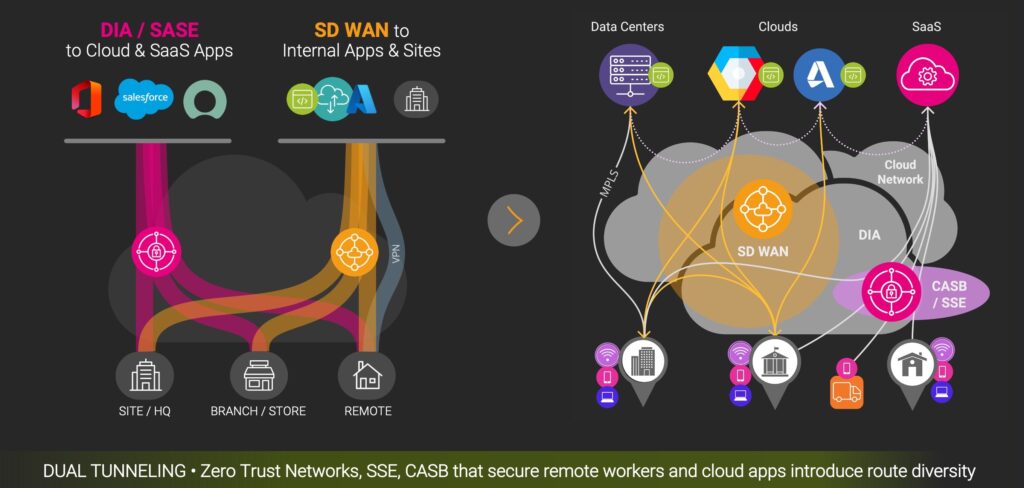
Many of our customers using SaaS and cloud applications are looking for ways to improve the experience of their users by migrating away from VPNs and private connection to SASE security platforms. Compared to a relatively simple VPN and firewall deployment, SASE (Secure Access Service Edge) combines a range of complementary web-hosted security functions including Secure Service Edge (SSE), Secure Web Gateways (SWG), Cloud Access Security Brokers (CASB), Zero Trust Network Access (ZTNA), and in some cases, SD WAN.
Despite its complexity, we are seeing widespread evaluation and adoption of SASE security solutions–in whole in or part–from Zscaler, Netskope, Palo Alto (Prisma), Cato Networks, Fortinet, iBoss, Symantec (Broadcom), VMware and Forcepoint, in addition to offerings from Cisco and Microsoft. In a SaaS and cloud-centric world, cloud security, internet security, and zero trust access are better deployed in an integrated manner, hence the popularity of SSE and SASE security solutions.
The Origin of SASE, from Access to Zscaler
Each SASE solution has different strengths and weaknesses, largely depending on how their platforms were originally developed. Zscaler and Netkope started in the cloud security space, whereas Fortinet and Forcepoint evolved their firewall solutions towards SSE. Cato and Cisco integrated SSE into their SD WAN networking platforms.
The one thing they all have in common? Intermittent performance issues, difficult troubleshooting scenarios, and a new layer for SecOps, IT and network operations to deploy, monitor and optimize. Teamwork is necessary to optimize SASE solutions, as SSE, ZTN, SWG and CASB performance issues can impact multiple groups within IT.
Let’s explore why SASE is essential for hybrid working performance, what causes performance issues, and how to detect, diagnose and fix them.
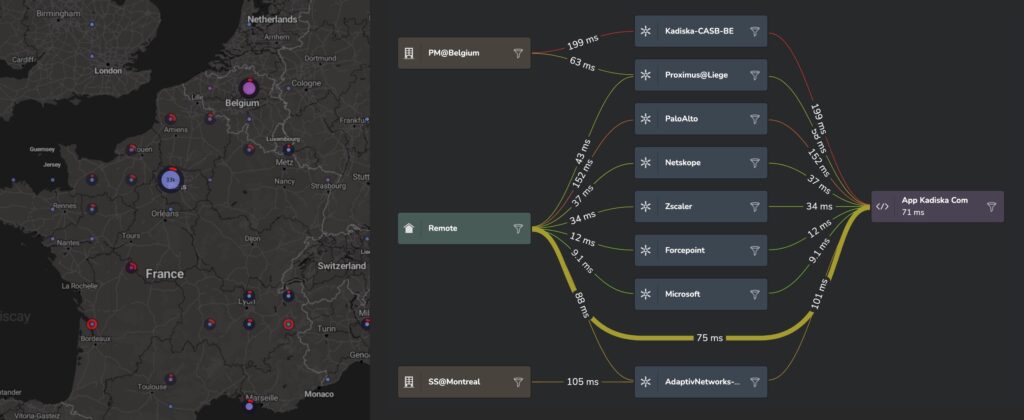
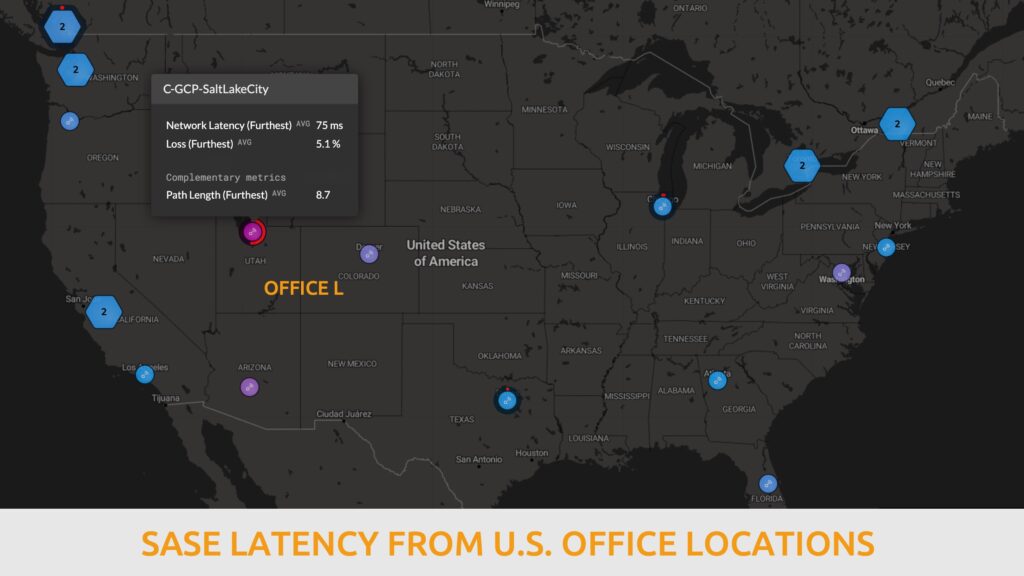
SASE performance by Zscaler, Netscope and other vendors by region in Europe
SASE Security, A New Digital Enterprise Essential
It’s becoming clear that some form of SASE is essential when faced with a highly distributed workforce, cloud hosting, SaaS and private applications. In 2021 Gartner predicted that by 2024, at least 40% of enterprises would have explicit strategies to adopt SASE. Two years later, they now expect 75% of enterprises to have SASE in place by the end of next year.
Interest in SASE was originally accelerated by the pandemic, followed by the formalization of digital workplace initiatives and part-time return to office policies. The result is that hybrid work is here to stay for over 75% of employees in North America and Europe, and SASE is an effective way to address performance issues hybrid working introduces
SASE Performance Advantages vs. New Issues
While SASE is supposed to deliver better user performance than traditional VPN and secure web gateways (SWG), enterprise IT teams often find that it is difficult to detect SASE-related issues, and that whether Zscaler, Netskope, Fortinet or Palo Alto, integrated monitoring and traditional tools are often insufficient to troubleshoot incidents and optimize end user digital experience within reasonable timeframes.
It is also difficult to detect users and applications that bypass SASE with direct internet connections–whether intentionally or due to endpoint configuration issues—and to ensure dual tunneling configurations are working as expected. The result is compromised security, and another point of vulnerability across on-site and remote workers locations.
How SASE Can Impact Employee Productivity and Digital Experience
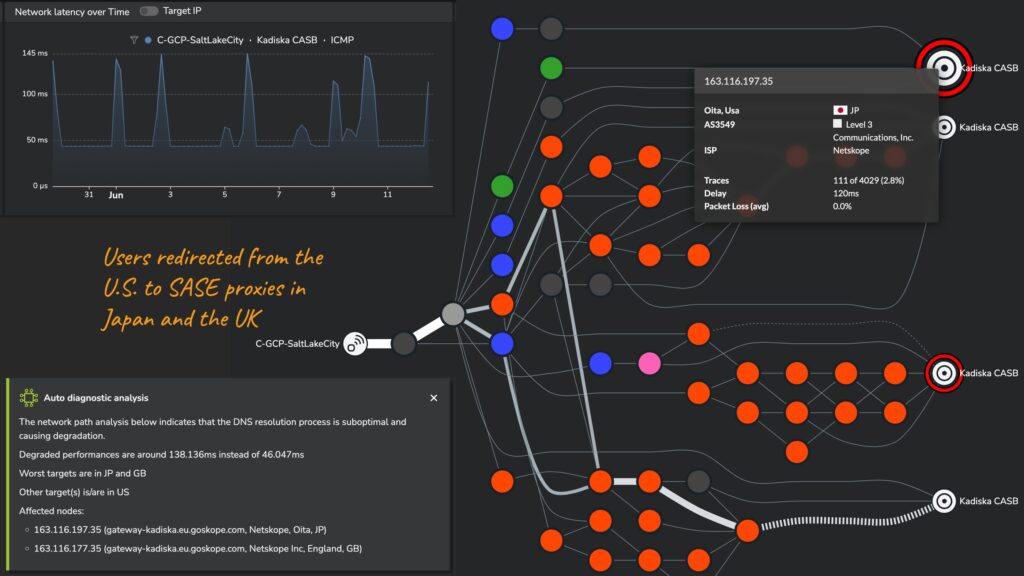
The main origins of SASE performance issues are implicit to its architecture, and are common to all vendors’ offerings without exception. We regularly see Netscope, iBoss, Fortinet, Zscaler, Microsoft and many other solutions introducing high latency, redirection delays and packet loss.
These issues are often straightforward to resolve, but only if the problems can be detected to begin with. With many components sometimes hosted in different cloud locations, issues can arise separately in SSE, SWG, ZTNA or CASB functions, making detection and troubleshooting more complex.
Three Causes of SASE Performance Issues
Which solution performs best in any given context depends on three main factors:
- Network connectivity from the user sites to the SASE point of presence (proxies)
- Security processing within the SASE platform
- SASE configuration (fail-over , traffic bypass, prioritization, deployment method)
1. Proximity and Connectivity to SASE Nodes
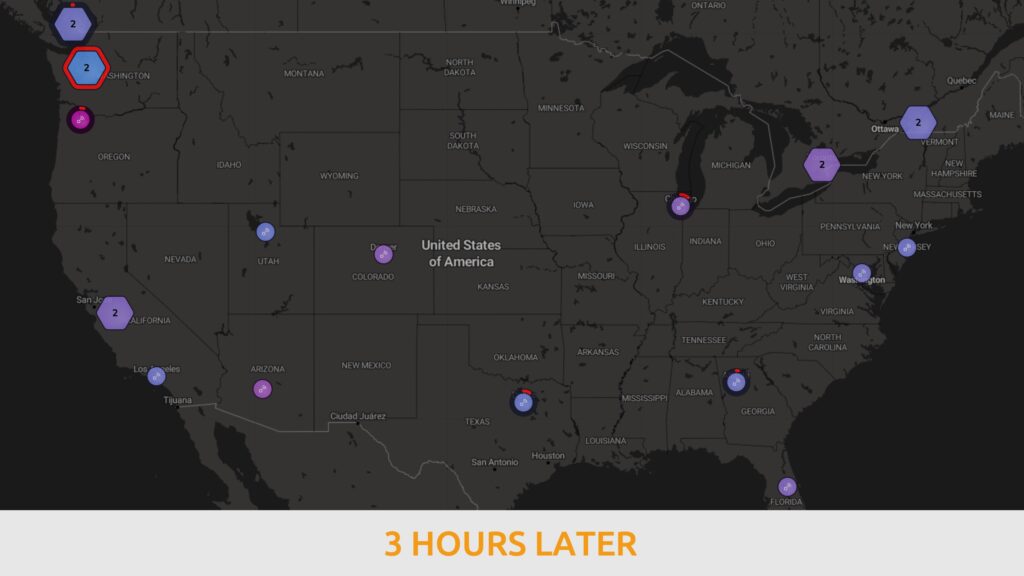
In a widely distributed group of users (from a geographical and connectivity perspective), the latency between users and the SASE entry point can be significant, ranging from several to hundreds of milliseconds.
This end to end latency can be impacted by degradations occurring within:
- LAN / WiFi
- ISP last mile (access network)
- ISP backbone
- Peering between ISPs, service providers and cloud networks (subject to BGP routing policies between autonomous systems (AS)
- Redirections directed by the SASE platform itself:
- DNS resolution controlled by the SASE
- Ideally steers users’ traffic to the “closest” SASE PoP
- Route and latency can be impacted by user geolocation errors and SASE platform load balancing policies
From an enterprise IT perspective, the easiest ones to optimize are:
- Your own WiFi / LAN infrastructure
- Your ISP’s last mile, backbone and the peering issues (you can switch providers, or SD WAN capabilities to prioritize the best performing connection)
2. SASE Security Function Processing Performance
SASE traffic processing introduces latency and can degrade application responsiveness, impacting employees’ digital experience. Security processing delays can vary depending on the platform, PoP / proxy location, the application and the type of transaction between users’ browsers, clouds and applications.
Some SASE capabilities introduce more latency than others, listed here from high to low impact:
- ZTNA / Cloud Firewalling
- Secure Web Gateways / Cloud proxies
- DLP (Data loss prevention)
- CASB (Cloud Access Security Broker)
Some SASE solutions will give you insights into the “processing cost” of your policies, some will not. Understanding the performance overhead of your security policy (by comparing flows where different policies are applied) is a best practice to make sure the performance impact is bearable to employees.
3. SASE Configuration and Deployment Models
The performance impact of SASE configuration and deployment methods can vary significantly depending on the specifics of the implementation.
- Fail-Over Settings: Choosing between availability or low latency can impact performance. Availability-focused settings ensure constant access but might increase latency, leaving users connected to distant PoPs for extended periods, while low-latency settings favor quick data transfer at the risk of decreased availability.
- Traffic Bypass for Latency-Sensitive Applications: This improves performance by allowing fast data transfer from specific applications, though it can introduce potential security risks as precise configuration is often difficult.
- Application Prioritization: Allocating more bandwidth to critical applications ensures their performance under heavy network loads, but may reduce resources for other applications.
- Deployment Methods: Hardware agents can offer high performance but lack scalability and adaptability compared to software agents which balance performance and flexibility.
- Policy Configuration: Granular policies demand more processing power, which could impact performance.
- Multi-tenant vs. Single-tenant Architecture: Multi-tenant architectures are cost-effective but could face ‘noisy neighbor’ issues. Single-tenant architectures offer better performance but at a higher cost
Additional Factors Impacting Digital Experience
When users access applications through a SASE platform, the SASE platform is only one component of the overall digital infrastructure that can impact digital SaaS, cloud and web application and connectivity performance.
It is important to keep a wide angle view of user performance and keep all the factors at view to optimize employees’ digital experience:
- Endpoint performance: each endpoint can be saturated at different times and levels (CPU, RAM, drive access, competing processes, etc…)
- Local area network / WiFi: how users are connected to the WAN infrastructure is another common bottleneck
- SaaS and cloud connectivity performance: while not all SASE platforms have the right presence in all regions where your users are located, not all SaaS providers provide an equal service in every region of the world. The connectivity from local SASE PoPs can be the source of slow service for the user.
- SaaS and cloud application performance: like any application, SaaS platforms can provide different levels of responsiveness depending on the time, the transaction requested and the parts of their platform which are at work (CDN, API gateways, TLS security, authentication, etc…)
Overall, to optimize remote access to cloud and internal apps, the best approach is to develop an end-to-end view which allows your team to drive optimization aligned with user impact, efficiently troubleshoot, diagnose and resolve issues, and validate the outcome.
Detecting, Troubleshooting and Resolving SASE Performance Issues
Network performance and Digital Experience Monitoring (DEM) are essential tools to identify, diagnose, and resolve SASE performance issues. They provide visibility into the performance of network services and applications, user experiences, and the overall health of the network infrastructure.
This user-to-application vantage point quickly identifies the root cause of SASE performance issues across endpoint, network, SASE capability (SSE, SWG, CASB, ZTNA, SD WAN, etc.), allowing the right team to focus on resolving the issue. This often requires collaboration with the SASE provider, who will be much more responsive when presented with detailed information about where problems originate, which applications and users they impact, and when and how often they occur.
How Digital Experience Monitoring Helps Fix SASE Performance Issues
Identifying Issues: Network path and performance monitoring can detect performance issues such as high latency, packet loss and route changes by mapping out the network path between users and applications, and reporting performance in real-time across all network segments and services (WiFi, ISP, SASE, SD WAN, private and cloud networks).
DEM complements these capabilities with end-user experience metrics like application availability, response times, page load times, and transaction times. Combined, they offer a comprehensive view of network performance from both the infrastructure and user perspectives, making it easier to identify any anomalies and the scope of their impact.
Diagnosing Issues: Once an issue is identified, DEM and network monitoring can help diagnose its root cause. This could be due to issues such as network congestion, improper SASE configurations, inefficient encryption/decryption, or hardware problems.
By correlating network metrics with user experience data, these tools can accurately pinpoint the cause of the problem. AI-based auto-diagnostics can help identify the root cause of issues within seconds.
Resolving Issues: After diagnosing the problem, these tools can guide network engineers towards appropriate solutions. This could involve adjusting SASE configurations, rerouting traffic, upgrading hardware, addressing endpoint or WiFi issues, or optimizing application performance.
Preventing Future Issues: Network monitoring and DEM can also proactively identify potential performance bottlenecks before they significantly impact the user experience. For example, they might detect specific SASE nodes, network paths or ISPs that are starting to degrade before they adversely impact application performance.
Optimize SASE Performance for Your Users
Network and digital experience monitoring provide valuable insights into SASE performance, enabling quick identification, diagnosis, and resolution of issues, while also aiding in proactive network management.
Kadiska’s digital experience platform offers transparency across internet-based SD-WAN, Content Delivery Networks (CDNs), and SASE/CASB-secured networks.
Setup your own account and give it a try. We’ll help you perform a SASE performance assessment to get you started.