Monitoring the impact of CASB on SaaS Performance can help you optimize a secured SaaS access and allow an efficient WFH / Remote work infrastructure.
The goal of this article is to summarize what CASB is and explain why it can affect digital services performance through two real live examples.
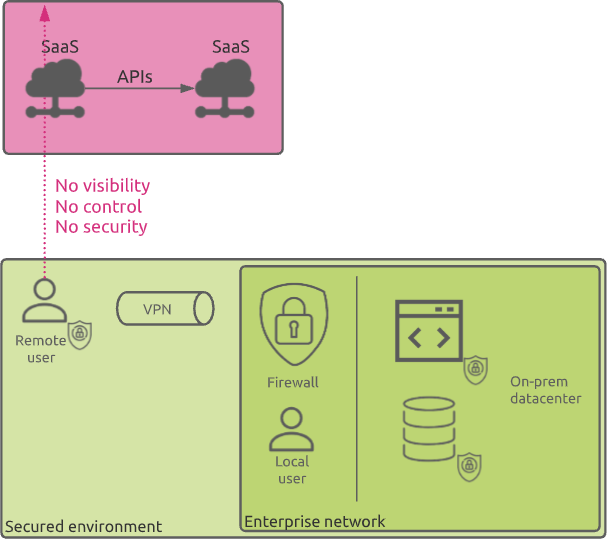
From the very beginning of the cloud computing era, security has been one of the main concerns among enterprises that are considering the public cloud. For many organizations, the idea of storing data or running applications on infrastructure that they do not manage and control seems inherently insecure.
In an on-premise IT environment, the security perimeter is quite easy to control. On the other hand, the cloud opens new paths of communication and data exchange that are by nature and default totally out of control of IT teams.
What is a CASB?
CASB stands for Cloud Access Security Broker. It provides enterprises with a critical control point for the secure use of cloud services across multiple cloud providers.
It focuses on four core pillars:
- 1. Visibility – Detect all cloud services, assign each a risk ranking, identify all users and dependencies with third-party applications
- 2. Data security – Identify, classify and control sensitive information
- 3. Threat protection – Offer Adaptive Access Control (AAC); provide User and Entity Behavior Analysis (UEBA); mitigate malware
- 4. Compliance – Supply reports and dashboards to demonstrate cloud governance; assist efforts to conform to data residency and regulatory compliance requirements
So, CASBs address a critical enterprise requirement to set policy, monitor behavior and manage risk across the entire set of enterprise cloud services being consumed (including SaaS applications, collaboration and videoconferencing suites and internal applications hosted on premise or in the cloud).
Gartner’s 2020 security spend forecast predicts a significant, but slowing growth rate for CASB: 37.2% in 2021, 33.2% in 2022, 32.0% in 2023 and 30.5% in 2024. Although the forecast predicts slowing spend for all security markets, CASB’s growth remains higher than any other information security market (see Forecast: Information Security and Risk Management, Worldwide, 2018-2024)
How CASBs work
One of the major decision factors when choosing a CASB solution, if not the only one is the list of capabilities that each provider offers. Services can include authentication, SSO (Single Sign On) and IAM (Identity and Access Management) integration, authorization, credential mapping, device profiling, data encryption and key management, logging, alerting, data loss prevention, configuration auditing, and malware detection and prevention to name a few.
Nevertheless, one aspect that is often underestimated, and difficult to apprehend upfront, is the performance impact that accessing cloud services through a CASB will have! In clear how slower or faster will it be for your WFH / remote users to access their SaaS applications. Will your CASB boost or deteriorate your SaaS performance?
To understand this impact, let’s first have a look at how a CASB works.
There are two key ways that a CASB can operate. It can be set up as a proxy — either a forward or a reverse proxy — or it can work in API mode, using cloud providers’ APIs to control cloud access and apply corporate security policies. Nowadays, CASBs tend to use both proxy and API technologies to benefit from their respective advantages.
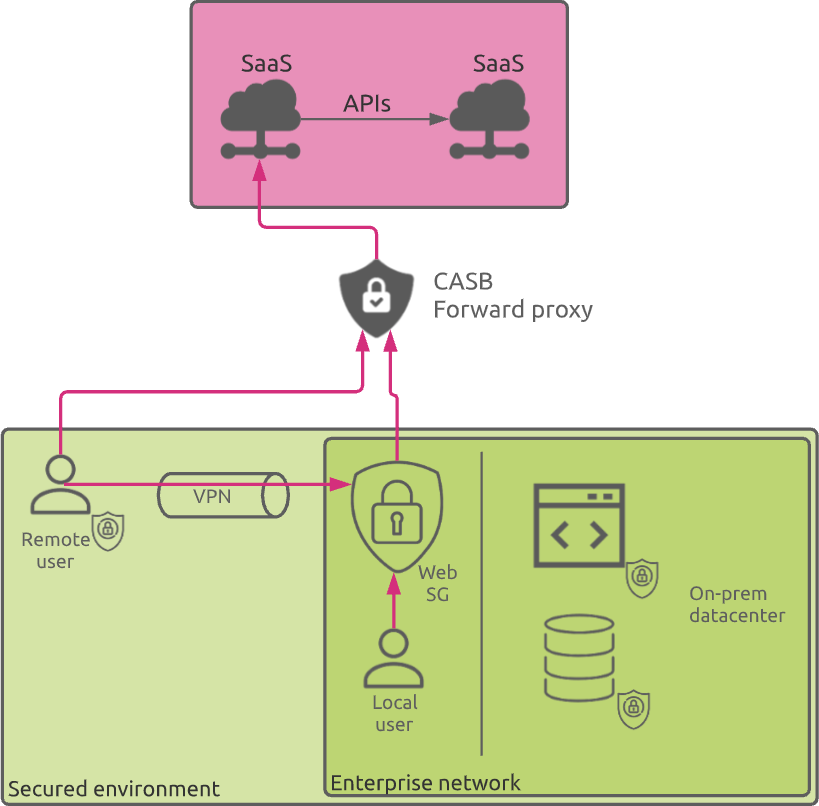
Forward Proxy
In a forward proxy model, all data between clients and the cloud are directed to the CASB for policy enforcement. For this model to work, organizations can configure their web security gateways or web proxies to route all outbound web traffic to the CASB. Alternatively, end-user devices can be configured with an endpoint agent that routes all web traffic to the CASB.
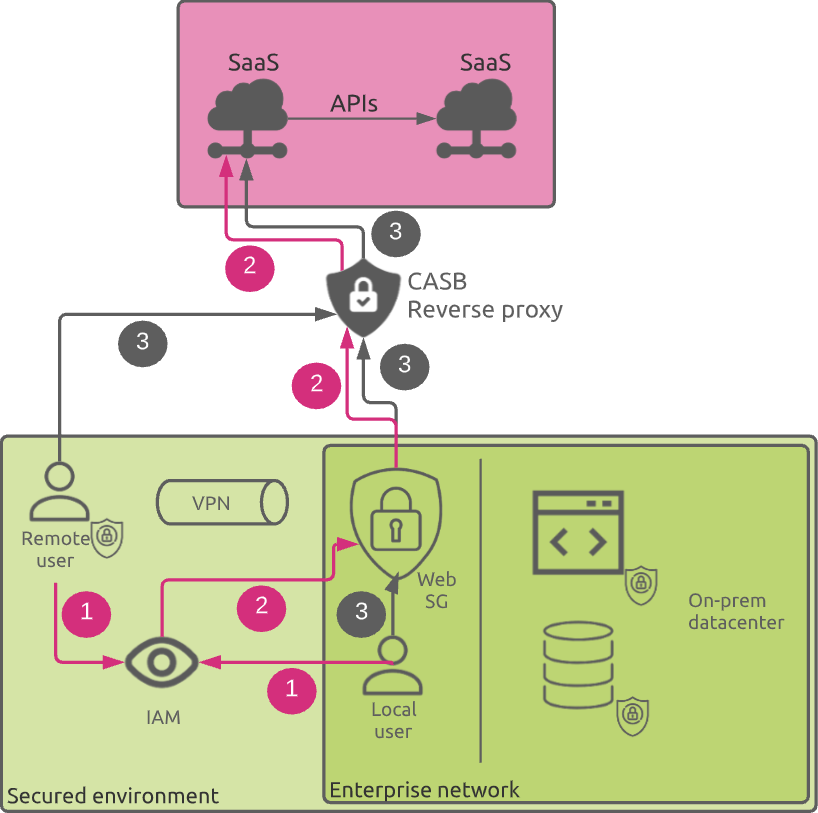
Reverse Proxy
The reverse proxy deployment model routes all traffic to and from a particular cloud service provider through the CASB. This model requires an Identity and Access Management (IAM) platform to forward authenticated user traffic to the CASB, which, in turn, seamlessly forwards the traffic to the cloud service provider.
The main advantage of this model compared to its counterpart “forward proxy” is that it does not require any special configuration or agent installation on the users’ devices.
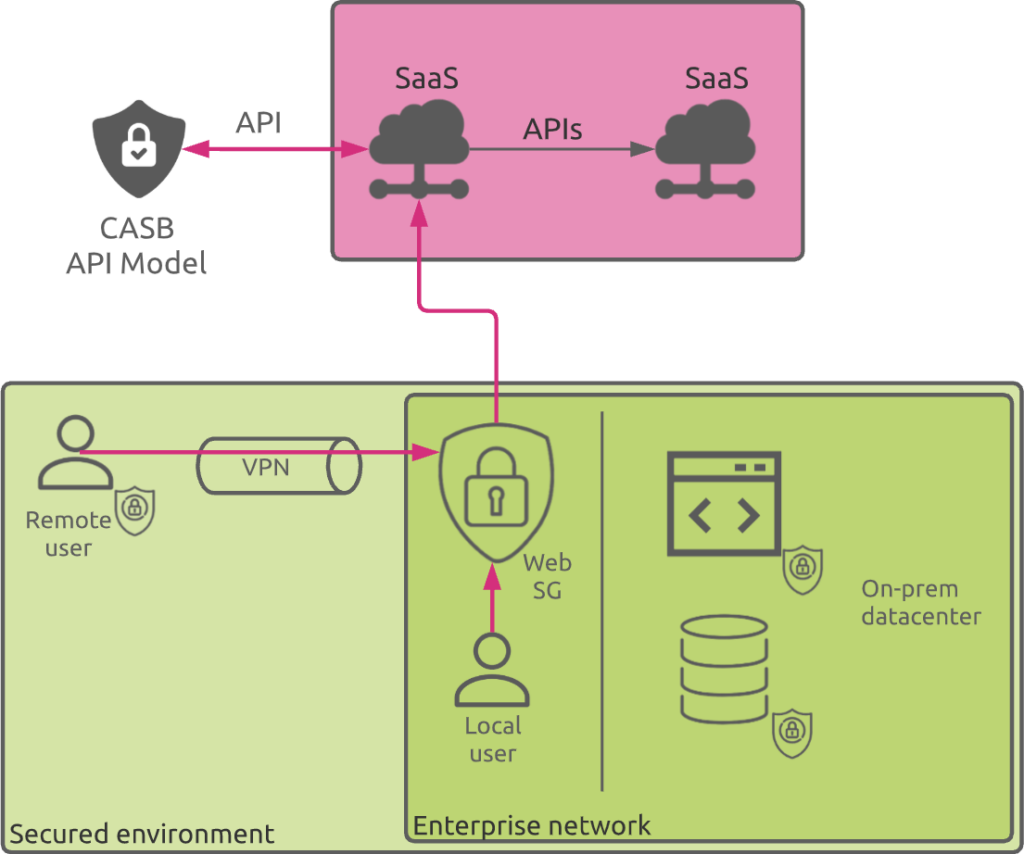
API-Based Systems
The API model requires an API connection established between the CASB and the cloud service / SaaS provider. The capabilities offered by the API model vary for each cloud service provider and not all of them support API integration.
Conclusion
CASB typically uses a combination of APIs and forward proxy for managed devices, and reverse proxy for unmanaged devices to control cloud access for users.
Some of the major players in the CASB market are:
- Netskope
- McAfee
- Palo Alto Networks
- Cisco
- Proofpoint
- Bitglass
- Symantec
- Microsoft
- Fortinet
- CipherCloud
- StratoKey
- Forcepoint
Now that you know more about what CASB means and the benefits of using it, let’s now see why it can impact your digital services performance.
What’s the performance impact of a CASB on SaaS and Cloud Services?
From the CASB concepts explained above, it is clear that the path between the users and cloud services is being impacted when using a CASB. All flows are being first directed to the CASB before reaching the cloud.
What does it mean from a SaaS performance standpoint?
First, the CASB should guarantee delivering the service as close possible to the remote users through local PoPs (Points of Presence).
Secondly, the network path between users and their allocated PoP should guarantee an appropriate level of quality in terms of network latency and packet loss.
If you intend to make use of CASB services, make sure you can monitor these elements, as you would be surprised to see how the connections to CASB PoPs can be inefficient and/or unstable.
To demonstrate this, let’s have a look at two real life examples.
Dynamic CASB PoP change
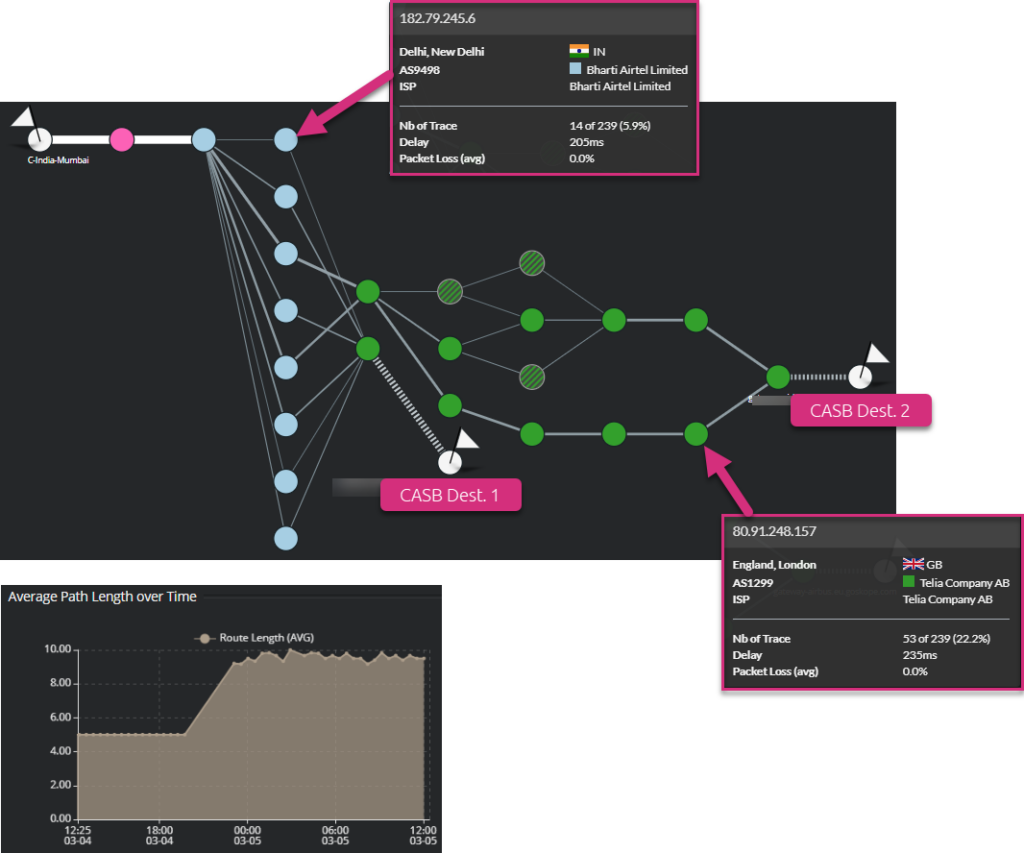
The following screenshot shows users located in Mumbai (India) that connect to their CASB PoP.
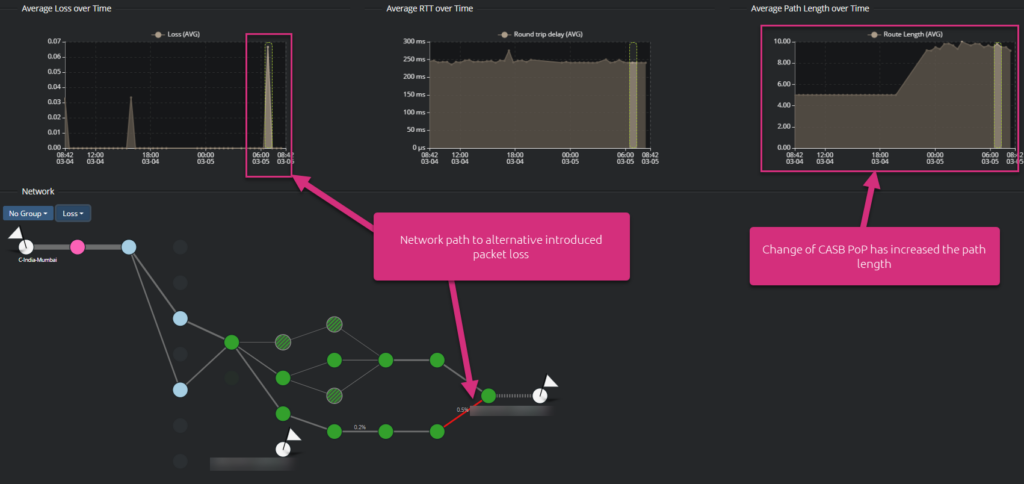
They traverse two operators (Airtel and Telia) to reach the CASB. From the “average path length over time” graph, you can see that the network path length has suddenly increased from 5 hops to around 9 hops (this refers to the number of routers on the path between the user and the PoP and largely affects latency). This corresponds to a switch of the CASB PoP location from CASB Dest. 1 to CASB Dest. 2.
This shows how dynamic the connection to a CASB can be. This behavior can add network latency and / or introduce additional packet loss. At the end, this can degrade digital services / SaaS performance. Here, routing within the Telia autonomous system is much more dynamic for the CASB Dest. 2 PoP connection.
In this particular case, the following screenshot highlights that switching from one path to another had no significant impact on the network latency. Nevertheless, this alternative path has experienced a peak of packet loss, which can be clearly identified.
CASB PoP reachability
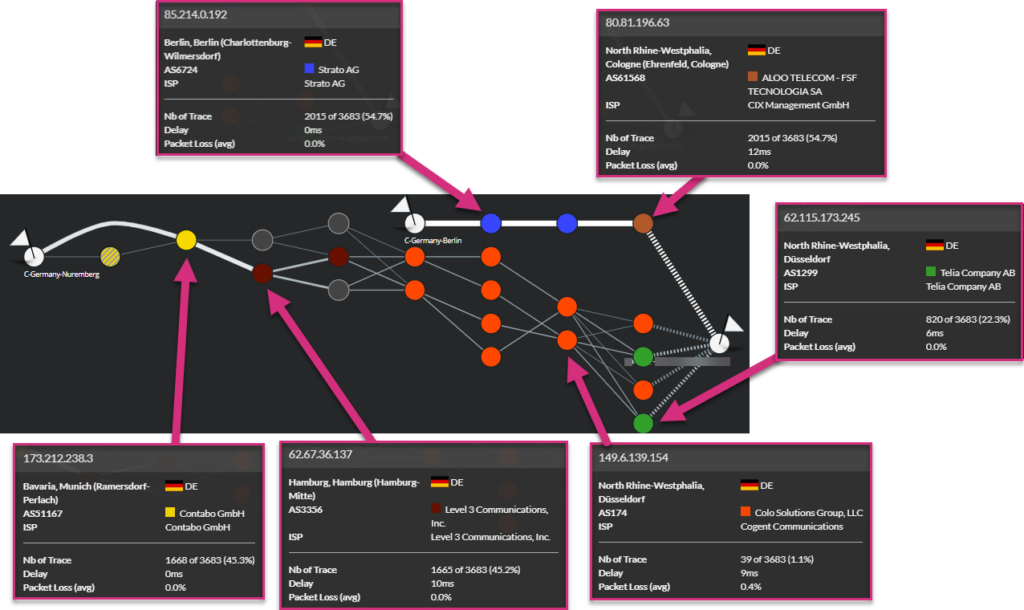
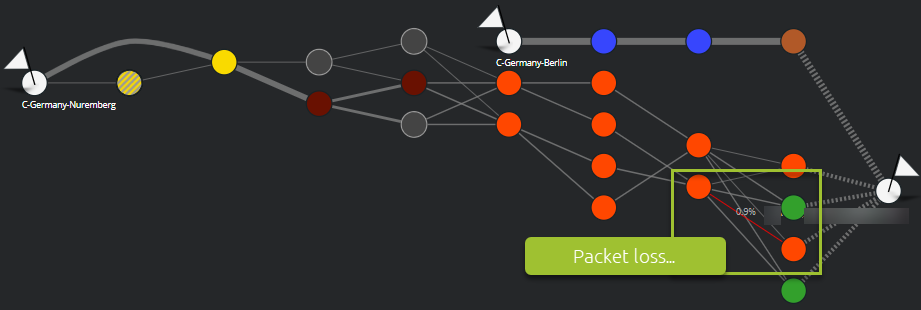
The following example shows how users in Germany (Berlin and Nuremberg) connect to their local CASB PoP.
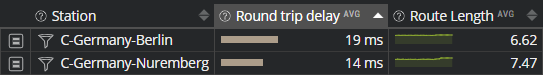
The users located in Nuremberg traverse a lot more different operators compared to the users in Berlin.
In this case, you would certainly think this can increase network latency for users in Nuremberg. In fact, measures show that this is not the case:
For this specific case, consecutively traversing autonomous systems from Contabo, Level 3, Cogent and Telia is faster than traversing only Strato AG and Aloo Telecom.
Nevertheless, we notice packet loss inside the Telia network. This only affected users in Nuremberg:
Takeways
Relying on CASBs services becomes mainstream for enterprises willing to embrace a multi-cloud based digital services strategy. Nevertheless, using CASB will impact the performance of SaaS and digital services.
One of the major business drivers for choosing the right partners should be the performances that they can guarantee. So to make the right decision you should identify:
- Where your users are located
- Where the CASB PoPs are located
- How your users will be directed and how efficiently they will be connected to these PoPs.
Once your choice is done, you better monitor your users’ connections to identify common faults like:
- Potential misconfigurations leading to connections to the wrong PoP(s)
- Operators that do not deliver the right level of network connectivity quality or routing efficiency
- Any temporary degradation due to network path changes, specific network operators outages or local CASB PoP modification.
If you are interesting in knowing more about network latency and packet loss, and how they impact network performance, please have a look at the following article