To realize the importance of such a technology, it is important to understand how IT security has evolved over the past few decades. In this article, we particularly focus on the concept of “security perimeter”.
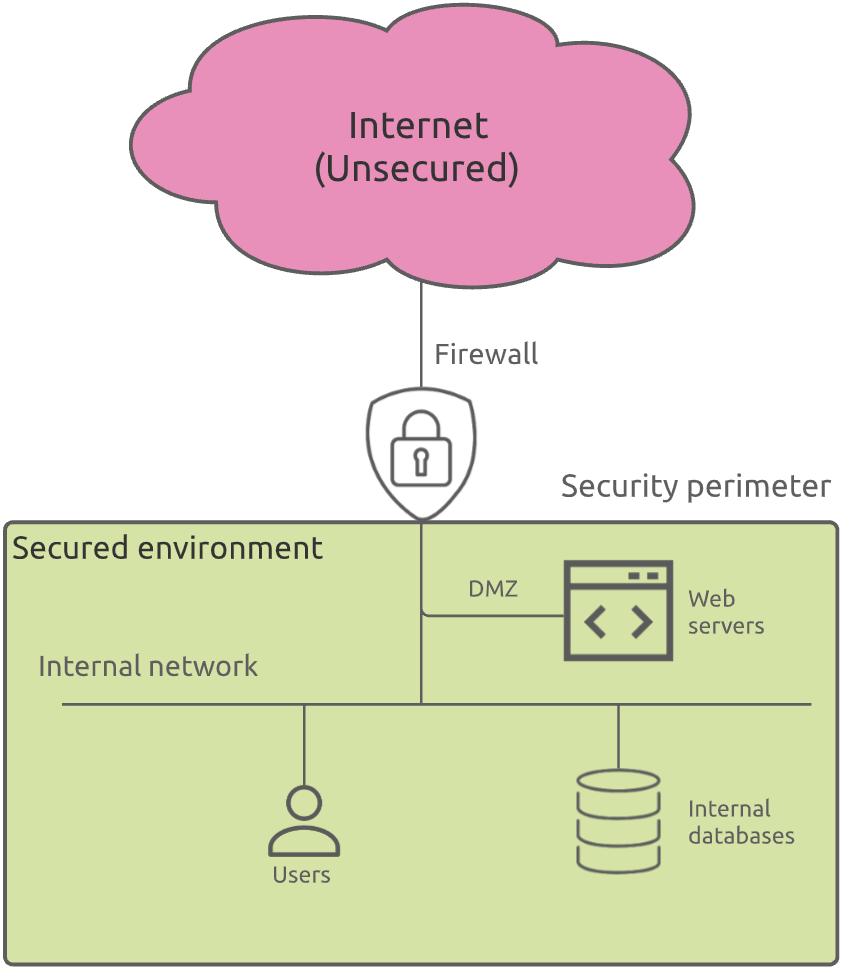
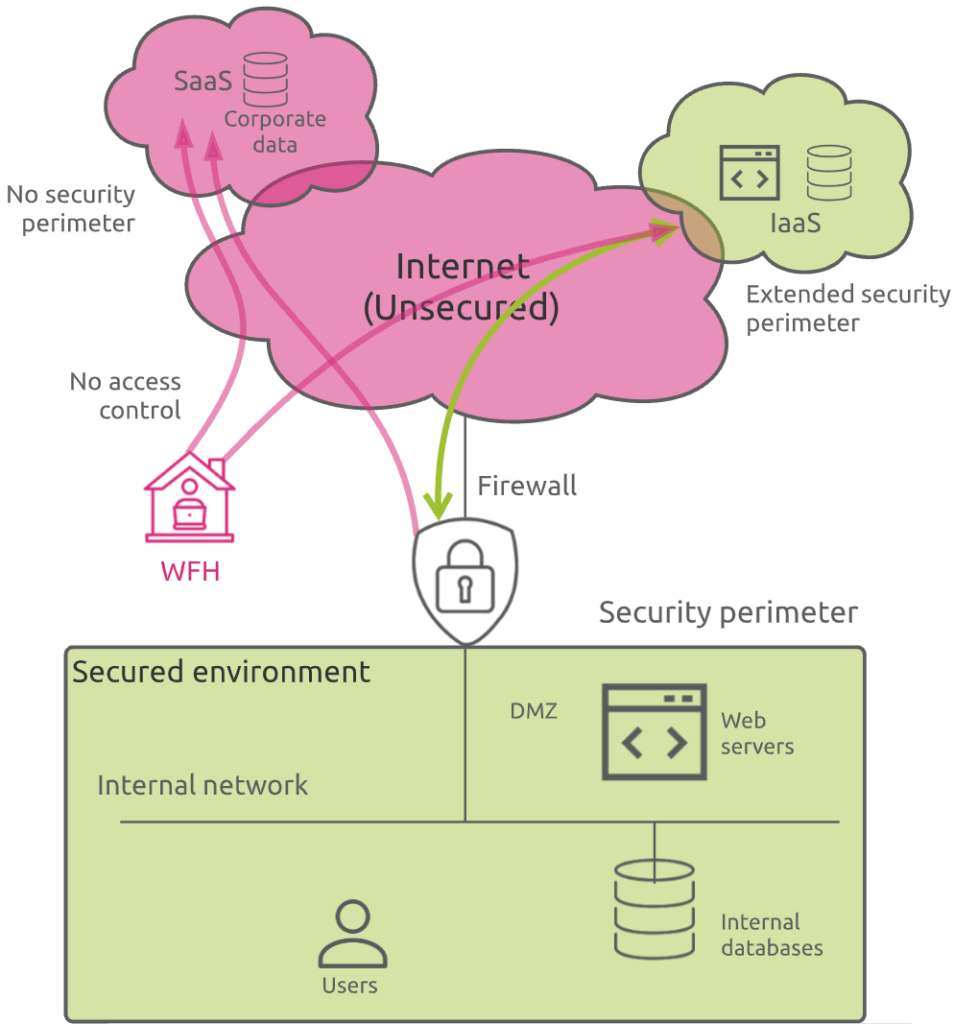
The security perimeter has always been considered as the demarcation point between the unsecure and wild external world (the Internet), and the safe and protected environment where all your corporate IT assets reside (the internal network).
In this context, the main question for organizations is how to prevent access to their IT resources from malicious external parties, as well as, in some cases, unhappy employees.
The good old days
I remember the time when defining a good security perimeter was quite easy. Your IT assets were located inside your corporate building and the access to and from the external world was limited to one or two internet access lines. You mainly focused on preventing the bad guys from entering your internal network.
This was the era of the firewalls. You typically defined a DMZ (DeMilitarized Zone) for directly accessible resources from the Internet, like web servers, as well as a highly protected internal network segment to host your internal business resources and users. This latter was not directly accessible from the Internet.
Eventually, you also wanted to prevent confidential information from leaving the company by implementing technologies like DLP (Data Leakage Prevention).
Things were clear and under control.
Time for more mobility: the WiFi
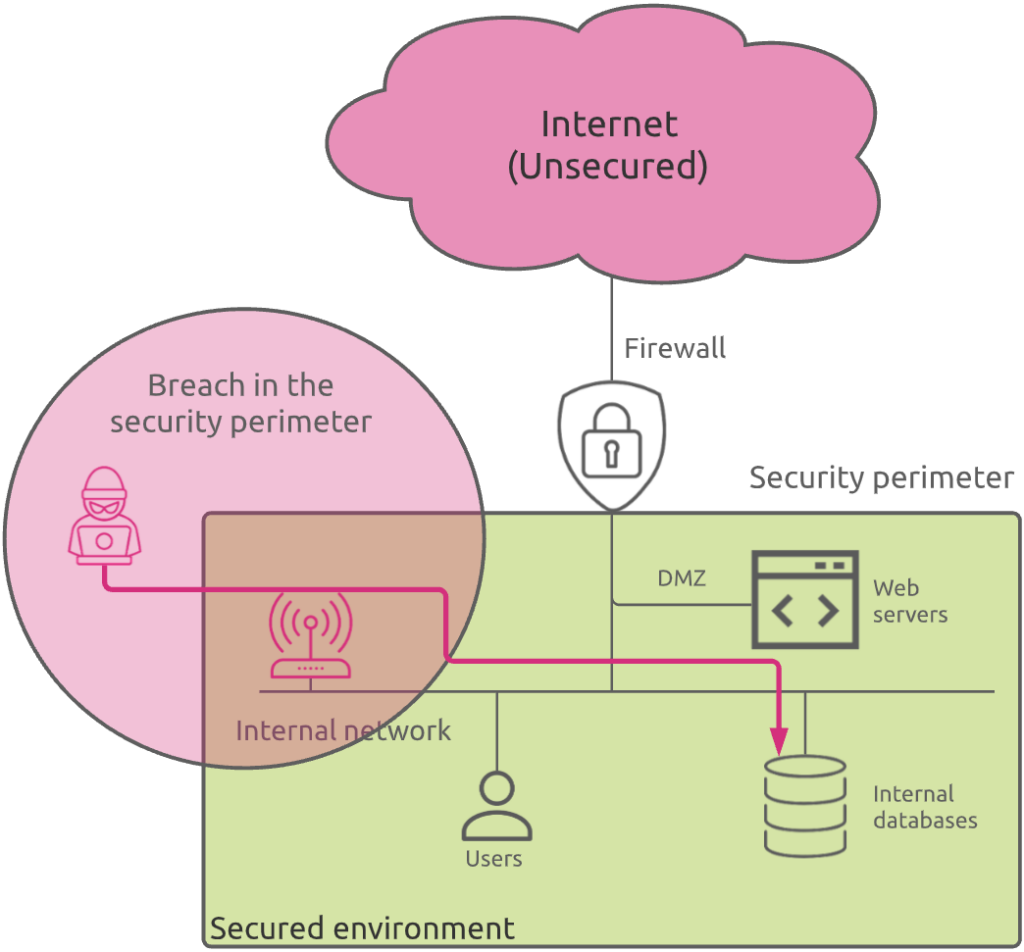
At that time, people were looking for more mobility inside their corporate environment. Being able to move from one meeting room to another with their laptop while staying connected on the network was a big step forward to more working flexibility. This is where WiFi came into play.
From an end user mobility perspective, it was great. But from a security point of view, this was the begin of the nightmare.
Indeed, the concept of perimeter was not so clear anymore. WiFi increased the internal network reachability while bypassing the first line of defense (the firewall).
In this example, a hacker located in the company’s parking could connect to the internal network and access corporate resources directly, without having to crack the firewall.
Dealing with WiFi networks and the new “Bring Your Own Device” (BYOD) trend was, unfortunately for security engineers, just the very beginning. The big bang was still to come.
The cloud era – first generation
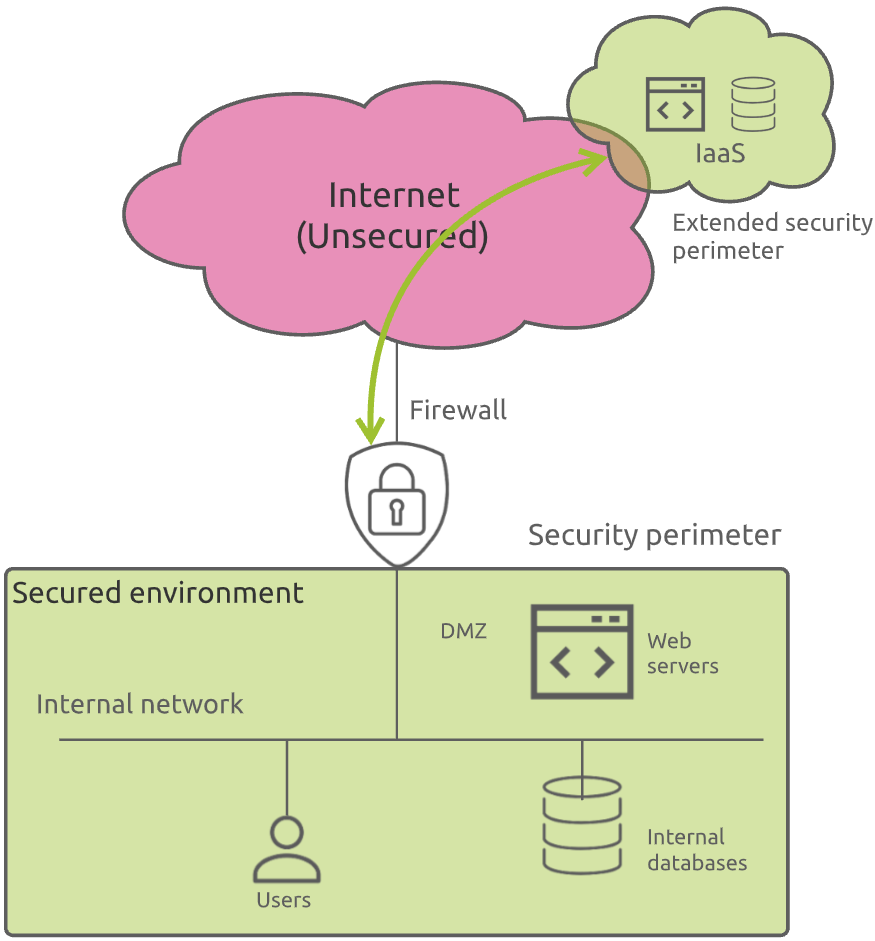
Some years ago, organizations began to find good reasons (less operations overhead, no need for on-premise datacenter infrastructure extension, costs, …) to move some first workloads to the cloud. At that time, the most popular type of cloud service was IaaS (Infrastructure as a Service). Basically, the cloud provider cared about the physical infrastructure, and you as a cloud customer, were responsible for deploying, securing, and maintaining your IT applications and data.
From a security standpoint, you can think of it as if the internal network was extended. The security perimeter extends as well and become decentralized.
Nevertheless, you could keep things relatively well under control. Communications between your corporate and your cloud infrastructures were secured through VPNs or specific links to the cloud providers and the data stored in your IaaS infrastructure could be secured the same way they were in your on-premises location (except obvioulsy the physical security that was handled by the cloud provider).
The cloud era – second generation
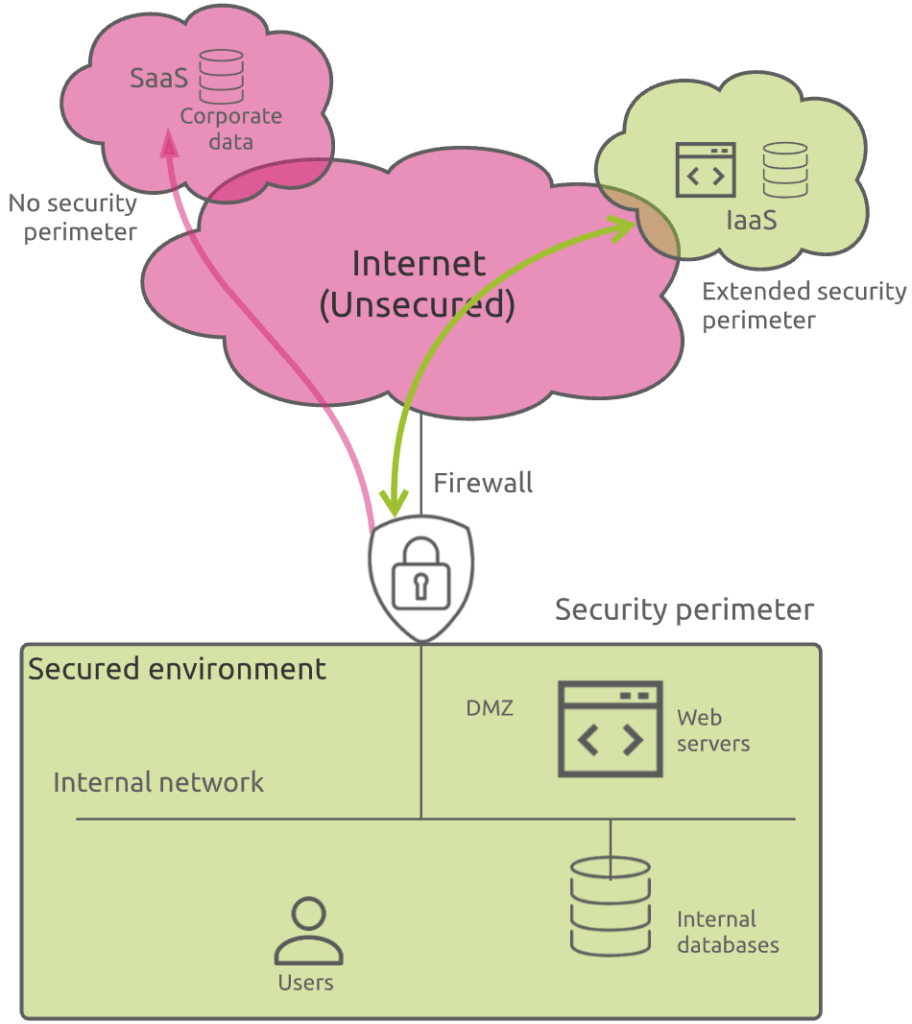
While cloud service providers extended their offerings to cover other types of infrastructures, like PaaS (Platform as a Service), software editors started to leverage cloud infrastructures unique capabilities to propose their services in a SaaS (Software as a Service) model. A well-know example is Microsoft Office 365.
The problem this time was that the concept of security perimeter itself totally disappeared. You, as an IT organization, did not manage the SaaS platform itself. Some of your corporate sensitive data were now hosted somewhere, in an environment you had totally no control over!
Your only solution was to rely on contractual clauses and SLAs with your SaaS provider…
Nevertheless, you were in spite of everything lucky in your misfortune: you could still control how corporate users connected to these SaaS applications.
New reality: Work From Home (WFH)
It is not a secret anymore: the new pandemic situation we all live in since 2 years has dramatically changed how people work. Work From Home becomes the standard for many organizations.
Even if some companies still rely on VPN to connect corporate users to SaaS through the secured corporate network, more and more users directly connect to SaaS applications from their home high-speed Internet connection.
In such a scenario, you end up loosing control of our corporate data. You do not only loose the security benefit of a security perimeter, you are unable to properly control how users access your corporate data.
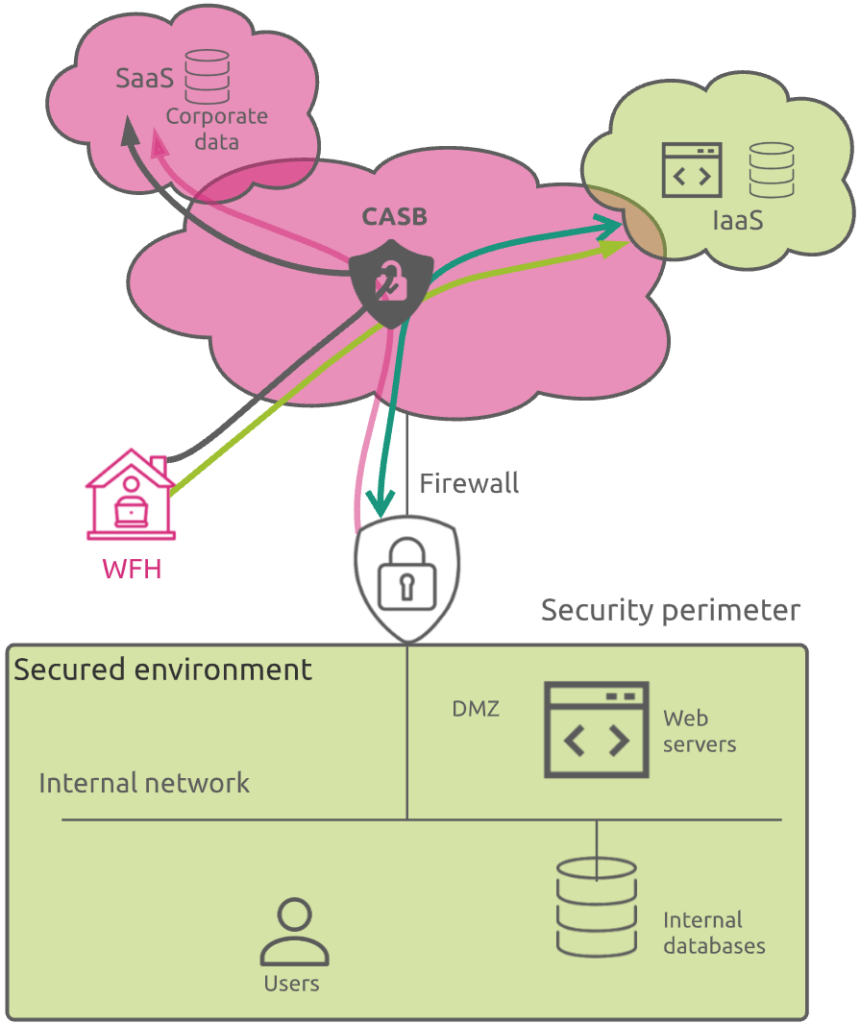
This is where CASBs play an important role.
Which benefits does a CASB bring
Even if it can be implemented as an on-premises software or hardware, a CASB is typically a cloud-hosted software that acts as an intermediary between users and cloud service providers.
It addresses most of the challenges mentioned above, across SaaS, PaaS and IaaS environments, and more.
Addressing the Shadow IT challenge
The first historical reason for using a CASB was to detect and control any usage of unapproved SaaS resources, called “shadow IT”. Using SaaS application is so easy that users and business owners started using unapproved applications, even without informing the IT team.
CASB allows enterprises to safely use the cloud by bringing full visibility in cloud activities and protecting sensitive corporate data.
It serves as a policy enforcement center, consolidating multiple types of security policy enforcement and applying them to everything your business utilizes in the cloud, regardless of what sort of device is attempting to access it.
Addressing the WFH challenge
While stemming the threats resulting from Shadow IT was a primary use case, it wasn’t the only reason that drove widespread adoption of CASBs.
As explained previously, many businesses move sensitive corporate data from on-premises datacenters to the cloud. In this scenario, a CASB helps protect both movement of data (by restricting things like access and sharing rights) and the data themselves (confidentiality) through encryption.
Capabilities
In its paper “How to secure cloud applications using CASBs”, Gartner defines the following top 10 CASB capabilities:
- Cloud application discovery and risk rating
- Adaptive access control
- Data loss prevention
- User and entity behavior analytics
- Threat protection
- Client-facing encryption (including integration with digital rights management)
- Pre-cloud encryption and tokenization
- Bring your own key (BYOK) encryption key management
- Monitoring and log management
- Cloud security posture management
So, in a nutshell, CASB definitely helps security teams to:
- Assess the risk introduced by unapproved cloud resources usage
- Increase security posture of approved cloud applications and resources
- Monitor usage and adoption of approved cloud services
- Control managed and unmanaged devices access to cloud services
- Gain visibility into compliance risk
- Add threat detection capabilities to cloud services
Gartner’s 2020 security spend forecast predicts a significant, but slowing growth rate for CASB: 37.2% in 2021, 33.2% in 2022, 32.0% in 2023 and 30.5% in 2024. Although the forecast predicts slowing spend for all security markets, CASB’s growth remains higher than any other information security market (see Forecast: Information Security and Risk Management, Worldwide, 2018-2024)
If you want to know more about the four core pillars of a CASB, how it works and the performance impact a CASB may have on your enterprise SaaS access, have a look at the following article.