In our article “How does BGP routing work?”, we explain the foundations that make BGP the protocol used in the backbone of the Internet. We also briefly explain why BGP is so vulnerable to misconfiguration, which can lead to high scale outages.
In this article, we address one of the biggest threats to BGP: the BGP hijacking.
Definition
The whole BGP protocol is based on the principle of trust.
It is built on the assumption that interconnected networks do not lie when they announce groups of IP addresses (called IP prefixes) they own. This principle makes it really vulnerable to malicious attacks.
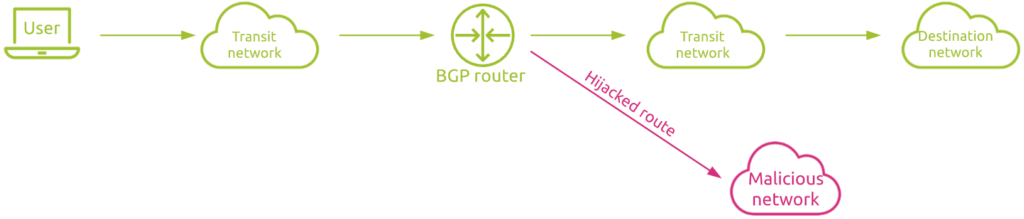
BGP hijacking is when attackers maliciously reroute Internet traffic. They accomplish this by falsely announcing ownership of IP prefixes that they do not actually own, control, or route to.
By broadcasting false prefix announcements, the compromised router may poison the Routing Information Base (RIB) of its peers and could propagate to other peers in a short period of time, to other autonomous systems (ASes), and onto the Internet. So identifying route IP hijacking as soon as possible is critical for the security of your network and your users experience.
How can BGP be hijacked?
BGP always favors the shortest, most specific path to the desired IP address. In order for the BGP hijack to be successful, the route announcement must either:
- Offer a more specific route by announcing a smaller range of IP addresses than other ASes had previously announced;
- Offer a shorter route to certain blocks of IP addresses.
Furthermore, the announcement must be made by the operator of an AS. So the attacker has to first compromise a legitimate BGP router.
To stay as much possible under the radar, attackers will frequently target unused prefixes to hijack. These will stay unnoticed for a while.
What happens when BGP is hijacked?
As a result of BGP hijacking, Internet traffic can go the wrong way, be monitored or intercepted, be ‘black holed,’ or be directed to fake websites. In addition, spammers can use BGP hijacking, or the network of an AS that practices BGP hijacking, in order to spoof legitimate IPs for spamming purposes.
One recent example from April 2021 is Vodafone Idea. The AS55410 from Vodafone Idea, an Indian operator based in Mumbai and Gandhinagar, was inundated with traffic, 13 times higher than average, leaving its users unable to access the Internet.
How can you detect BGP hijacking?
Without specifically monitoring how Internet traffic is routed, organizations are quite powerless to prevent or at least quickly detect BGP hijacks.
When a BGP hijacking occurs, in most cases, latency will increase significantly. This is due to the fact that hijacked network flows do not follow the most efficient route anymore, possibly traversing around the world unnecessarily.
So monitoring network latency and its impact on the users’ experience can help detect BGP hijacking.
This said, the best way today to detect BGP hijacking is by constantly monitoring the BGP routes taken by your network traffic. By doing so, you can immediately detect any abnormal route change.
How can you protect your organization against BGP hijacking?
MARNS – Mutually Agreed Norms for Routing Security
As stated above, protecting your organization against BGP hijacking is difficult. It requires vigilance, information exchange and best practices sharing across the globe.
This is where MARNS comes into play. It is a global initiative, supported by the Internet Society, that provides crucial fixes to reduce the most common routing threats.
Its foundations are built on four pillars:
- Filtering:
- Making sure your and your customers’ routing announcements are correct
- Stops false routing announcements from distorting the Internet roadmap
- Anti-spoofing:
- Enabling source address validation prevents spoofed packets from entering or leaving your network
- Coordination:
- Maintaining globally accessible contact information in common places such as the PeeringDB, RIR whois database, and your own website
- Global validation:
- Publishing your data, including your routing policy and prefixes you intend to advertise, so your routing information can be validated by third parties
Companies that own ASes are really encouraged to take part of this community.
BGPsec
BGPsec seems really promising. It is a BGP extension, defined in RFC 8205 and published in September 2017. It adds cryptographic verification for advertised BGP routes. With BGPsec, the backbone routers apply digital signatures to their route update advertisements. This makes it more difficult for unauthorized attackers to improperly advertise routes for ASes.
Unfortunately, BGPsec introduces a new major challenge that slows its adoption. Indeed, cryptographic verification implies an additional computational overhead on routers. This often requires upgrading the routers with a specific crypto hardware.
Seeing the high number of routers in the field, globally adopting BGPsec is not for tomorrow.
Configuration fine tuning
As an organization, you do not have to join the MARNS community or use BGPsec to already take concrete actions to protect your network. One of the common best practices is to filter IP prefixes.
Even if it remains quite difficult to enforce, most networks should only accept IP prefix declarations if necessary, and should only declare their IP prefixes to certain networks, not the entire Internet. Doing so helps prevent accidental route hijacking and could keep the AS from accepting bogus IP prefix declarations.
In our views, the very first step you should take is monitor the way your BGP AS can be reached and detect any discrepency or abnormal route change. To get started, read this article.